Openotp Credential Provider For Mac
Whether your nonprofit group is running a traditional auction, with paper bid sheets and paddles, or want to implement mobile bidding, SchoolAuction.net has you covered with a full-service auction-management system. Sell tickets, solicit donations, build your catalog, and print all the collateral you need before your event, then manage the entire event night, from check-in through check-out. Use our credit-card processor, or connect your own (must be compatible with Authorize.net or one of our other supported gateways).
The OpenOTP Credential Provider for Mac OSX is a component that integrates the RCDevs OpenOTP one-time password authentication into the Mac OSX login process. RCDevs OpenOTP Authentication Server is a WebApp that is tightly coupled to the RCDevs WebADM application server. For this recipe, you will need to have WebADM/OpenOTP installed. MultiOTP Credential Provider is a V2 Credential Provider for Windows 7/8/8.1/10/2012(R2)/2016 with options like RDP only and UPN name support credential-provider otp totp hotp yubikey motp multiotp sms authentication offline windows active-directory ldap cplusplus yubico-otp yubico yubikey-authenticators.
Normal Login flow Simple Login flow Push Login flow 1. Product DocumentationThis document is an installation guide for the OpenOTP Credential Provider for Windows.
When I received it, it had Mac OS 10.4 on it, but I have since wiped the hard drive and am installing my way back up to it (I'm currently on 10.3).However, I'm not sure how to install Mac OS 10.4 (Tiger) since it comes on a DVD, but this iMac doesn't have a DVD drive. I could probably scrounge up an iPod if I need to, but I'd also be interested to know if there are other ways to install Tiger on a Mac without a DVD drive. The original owner said something about how they put Tiger on an iPod to install it, but didn't remember the details. I have an iMac G3 that does not have a DVD drive, which was gifted to me along with install media for Mac OS 10.0-10.4. Mac os x 10.0 download.
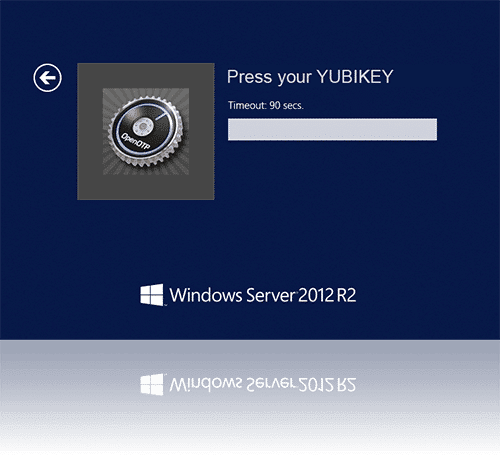
Hence, the installation or configuration of WebADM, including token registration is not covered in this guide. For installation and usage guides to WebADM refer to the RCDevs WebADM Installation Guide and the RCDevs WebADM Administrator Guide available through the. Product OverviewThe OpenOTP Credential Provider for Windows is a component that integrates the RCDevs OpenOTP one-time password authentication into the Windows login process. RCDevs OpenOTP Authentication Server is a Web Service that is tightly coupled to the RCDevs WebADM application server.For this recipe, you will need to have WebADM/OpenOTP installed and configured. Please, refer to and to do it. System RequirementsThe OpenOTP Credential Provider runs on any x86/x64 Windows platforms starting with Windows Vista and Windows Server from 2008 versions.Your environment should fulfill the following requirements:.
x86/x64 Windows 2008 Server/Vista or later. Workstation joined to AD domain or not.
Network access. An instance of WebADM and OpenOTP running in your network. Permanent connection to OpenOTP server’s network API.
NetBIOS over TCP/IP enabled and resolvable. DNS suffix set to match your AD domain.4. Preliminary InformationAdministrative/elevated permissions are necessary on any workstation to correctly set up and/or change the OpenOTP Credential Provider’s configuration.To correctly setup the provider, please gather the following information. You will need to enter during the installation process:. The URI(s)s of the OpenOTP web-service(s) (mandatory).
These URIs are mandatory, due to the client needs to know where the OpenOTP SOAP network API can be reached. They are entered as a comma-separated list. NoteAdministrative/elevated permissions are necessary on any workstation to correctly set up and/or change the OpenOTP Credential Provider’s configuration. Please, run the Windows PowerShell as Administrator. Right click on the Windows PowerShell then select Run as Administrator.5.1 Local InstallationFirst, you have to download OpenOTP Credential Provider.Extract files from the archive on your Windows machine(s), run the MSI file and click on Next.Accept the End-User License Agreement and click on Next.Now, you can select to install the Credential Provider as default. You may also change the default installation directory as you wish.Click Next when you are done.
NoteInstalling the provider as default disables all other credential providers on the target system. Only Credential Providers provided by RCDevs will be available for login.
If any problem occurs you can still log in with other providers using the Windows failsafe boot. It is possible to force OTP login in failsafe mode. This is covered later. To log in on a Windows Server through RDP client with a One-Time Password, OpenOTP Credential Provider should be installed by default on the remote host to perform an OTP login. While testing: Do not install as default provider! Before choosing OpenOTP Credential Provider as default provider, perform a login test!On this page, you have to configure at least one OpenOTP SOAP URL(s). Your WebADM SOAP endpoint should be: You can also define a Client ID referring to a client policy in WebADM.UPN Mode defines how the Credential Provider sends the username and domain to OpenOTP server:IMPLICIT: username and domain are sent separately.EXPLICIT: username and domain are combined to UPN format (user@domain.com) and sent to the server.
This requires that corresponding UPN is configured for the user in the AD/LDAP directory.Click on Next.On the next screen, you can define the authentication form. ImportantIn case of failure during the provider configuration or unreachable network, even failsafe mode will not help you to login to a workstation that is set-up to force the use of the Credential Provider.To register the Credential Provider enforcement, copy the following text to a new text file, name it register.reg and execute it. Windows Registry Editor Version 5.00HKEYLOCALMACHINESOFTWAREMicrosoftWindowsCurrentVersionAuthenticationCredential Providers'ProhibitFallbacks'=dword:1To disable and unregister the failsafe enforcement copy the following text. Windows Registry Editor Version 5.00HKEYLOCALMACHINESOFTWAREMicrosoftWindowsCurrentVersionAuthenticationCredential Providers'ProhibitFallbacks'=-6.
Online Authentication TestYou are now able to log in your Windows machine in MFA. Please log out and enter your LDAP Credentials on the first screen. WarningCA file can not be stored and used through shared folder/path like:STORAGEca.crtThis manual was prepared with great care. However, RCDevs S.A. And the author cannot assume any legal or other liability for possible errors and their consequences.
No responsibility is taken for the details contained in this manual. Subject to alternation without notice. Does not enter into any responsibility in this respect. The hardware and software described in this manual is provided on the basis of a license agreement. This manual is protected by copyright law. Reserves all rights, especially for translation into foreign languages. No part of this manual may be reproduced in any way (photocopies, microfilm or other methods) or transformed into machine-readable language without the prior written permission of RCDevs S.A.
The latter especially applies for data processing systems. Also reserves all communication rights (lectures, radio and television).
The hardware and software names mentioned in this manual are most often the registered trademarks of the respective manufacturers and as such are subject to the statutory regulations. Product and brand names are the property of RCDevs S.A.© 2020 RCDevs SA, All Rights Reserved.